Hi, I'm Govind Ramachandran
Crypto ✪ Web3 ✪ DeFi
Featured on Times of India
Influencer ✪ CIS Specialist
4x World Record Holder
Crypto & MF Investor
10x Microsoft & Azure Certified Expert | ITIL® 4 Specialist Certified | 44x IBM & Design Thinking Certified | SNOW | NOC/IMS/CIS Specialist | Digital & Social Media Marketer | Brand Promoter & Lead Generator. I have two passions in life: technology and computers. Luckily, I’ve spent the all these years doing both at the same time. Take a look at my journeys below.

What I Can Do
Crypto Token Management
I help investors optimize crypto token strategies for sustainable growth and returns.
Crypto Investment
I can build, deploy, and manage services without the need for on premises infra management.
Crypto Staking
I optimize crypto staking to maximize investor yield potential.
CIS Skills
I can build, deploy, and manage services without the need for on premises infra management.
Branding
My mission is to elevate your brand's presence by crafting memorable identities by its target audience.
Business Stratagy
I’ll help you optimize your business processes to maximize profitability and eliminate unnecessary costs.
Blogging & Web Creator
Write and publish articles, stories, or posts on specific niches, often on personal blogs, or content platforms.
Social Media Outreach
Develop and share content on social media platforms, such as LinkedIn, Twitter & Facebook, to engage audiences or brands, and build communities.
Design Concept
Empathize, ideate, prototype, test - user-centric innovation shaping impactful solutions.
My Blog & Articles
Crypto & Web3 Projects

Crypto & Web3 Projects
Crypto and Web3 projects are transforming how we use the internet by giving people more control over their money, data, and digital identity. Instead of relying on banks or big tech companies, these projects use blockchain technology to let users interact directly, whether it’s sending money, owning digital assets like NFTs, or using apps without giving up privacy. It’s all about building a more open, secure, and user-focused internet for the future.
Here are some websites where you can earn money by simply using your internet — and some of them are completely free to use!
- Join Intract Quest – discover top Web3 projects, complete simple tasks, and earn rewards like tokens & NFTs! 🎯
Join @ https://bit.ly/qstintrctgrk
Intract #Web3 #CryptoRewards #LearnAndEarn #CryptoCommunity #BlockchainJourney - 🔥 Hurry up! GOLD STRIKE is exploding on Telegram! 🚀
Spin, score, and earn your share of the airdrop!
🏆 Don’t miss out—PLAY NOW!
Join @ https://bit.ly/goldstriker
💎 Play. Win. Earn. It’s that simple!
CryptoGaming #EarnWhileYouPlay #FreeTON #TelegramGames
- Metopia – 🚀 Build your Web3 Identity!
Join @ https://bit.ly/metopiaxyz
🌐 Build. Learn. Earn. Grow !
Your on-chain journey starts here! - Rent Out Your Unused Internet and Earn Money
Join @ https://bit.ly/grassiogrk
Download the desktop app for boosted rewards and start earning today !
- Earn Free Yohi & USDT in the Game!
Join @ https://bit.ly/YohiCrypto
Join Yohi and earn airdrops and USDT with me.🤩💰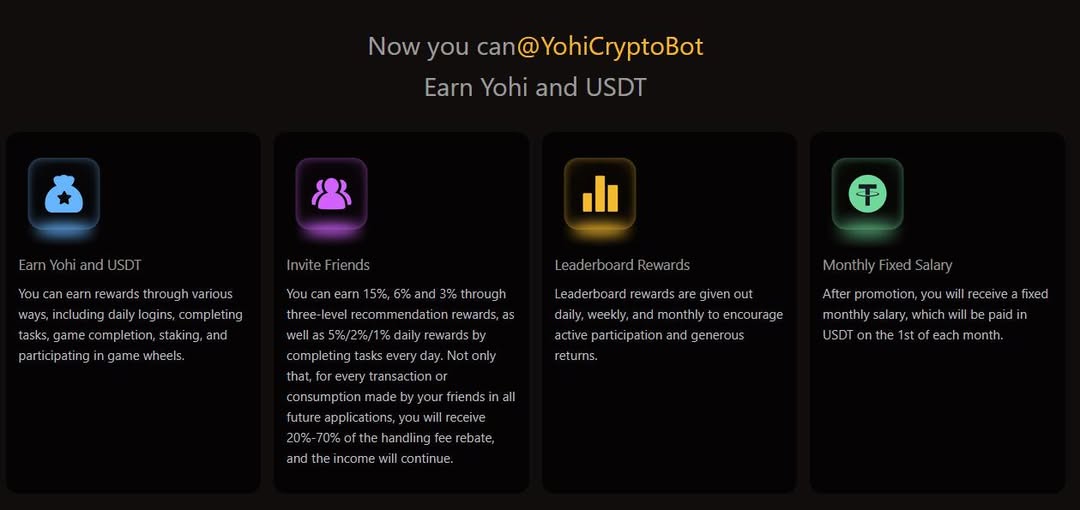
- Invite Friends to Earn Galxe Gold
Explore the exciting world of Web3 and start earning while you learn. Join Galxe through my invite link, complete fun quests, and unlock rewards like Galxe Gold. It’s the perfect way to grow your crypto journey and be part of the next big wave in blockchain innovation.
Join @ https://bit.ly/galxegrk
Learn More About Me @ https://www.govindrkannan.com/aboutme
Find My Crypto Verified Profile @ https://rarible.com/govindrkannan & https://ud.me/govindrkannan.x

Maximizing the Potential of Cloud Infrastructure: Strategies for Success
Maximizing the Potential of Cloud Infrastructure in today’s ever-changing world of digital marketing, nothing remains constant. Innovations are constantly being introduced, becoming integral parts of the business, cloud computing is also one such innovation. With cloud computing, you get incredible benefits of unparalleled scalability, unmatched flexibility, and iron-clad security. Compared to other traditional systems cloud computing helps businesses effortlessly adapt advanced technologies, making them more accessible and easier to support.
Getting the full essence of cloud infrastructure requires strategic planning, execution, and continuous optimization. Allowing your business to harness its capabilities together to effectively propel itself towards growth in the digital age.

Maximizing the Potential of Cloud Infrastructure
What is Cloud Infrastructure?
Cloud infrastructure is the first step in modern computing. it’s all about how businesses handle their IT resources and deliver their services. To understand cloud infrastructure, we need to know and understand what is cloud computing and how it works
Cloud infrastructure is the hardware and software that make cloud computing possible. Cloud computing means using the internet to get access to computing stuff like networks, servers, storage, apps, and services whenever you need them.
What are the main parts of cloud infrastructure?
The main parts of cloud infrastructure are
- Virtualization: This makes virtual copies of computer resources, so they are used efficiently and can grow and skim as needed.
- Networking: It makes sure everything stays connected so data can move smoothly between users and cloud services.
- Storage: It’s like a big, flexible storage space where data is kept safely and can be easily accessed
- Compute: This is the power to run programs and process data, all happening in virtual machines
The evolution of cloud infrastructure started around 2000 when companies began to think about using computing like a utility, just like electricity, Amazon took off with this idea in 2006 when they launched Amazon EC2, which let people rent virtual servers and storage whenever they needed.
Since then, cloud technology has grown fast. We now have things like Platform as a Service ( PaaS) and Software as a Service (SaaS), which give developers and businesses more ways to use and build applications on the cloud.
Types of Cloud Infrastructure:
There are a variety of cloud infrastructures that cater to different needs. The following are the most frequent kinds:
Public Cloud – This is the internet-based shared space that businesses rent out. It is an excellent option for small businesses or startups for a few factors. First and foremost, businesses only pay for what they utilize, which is ideal for businesses with low financial resources.
Private Cloud – I believe that one day I would own one complete cloud infrastructure just for me and my staff. It is ideal for large corporations or organizations with excellent safety measures.
Hybrid Cloud – this cloud combines the advantages of both public and private environments. It is an excellent resource if some materials are better placed in a private environment while others are better used in the public domain.
Advantages of cloud infrastructure
Understanding cloud infrastructure means learning the basic ideas, how it started, and the different ways it’s used today. When businesses use cloud tech smartly, they can do things more easily, grow quickly, and work more efficiently.
Cloud infrastructure is super important for businesses now. It gives lots of good stuff like making things run smoother, growing faster, and keeping things safe. Knowing these benefits helps us see why so many businesses are switching to cloud solutions.
Scalability and Flexibility
The biggest advantage of cloud infrastructure is how easily it can grow and change. Unlike old systems where getting bigger meant lots of time and money for new equipment, the cloud lets businesses update their tech as needed. This means dealing with sudden user growth or growing seamlessly.
Cloud providers offer resources that can grow and shrink. Such as virtual machines and storage. So, if you need more power for busy times or extra space for larger projects, cloud tech can do that easily.
Also, cloud systems can adjust resources based on how busy things are. This helps to manage everything smoothly and reduces costs
Cost-effectiveness
Another interesting benefit of cloud infrastructure is cost efficiency. Cloud services operate on a pay-as-you-go or subscription-based model, allowing businesses to pay only for the resources they use. This eliminates the need for large upfront investments in hardware and infrastructure, making cloud computing particularly attractive for start-ups and small and medium-sized enterprises (SMEs).
Also, cloud providers offer cost-effective pricing mechanisms to provide cost-effective pricing strategies to accurately calculate costs, reduce costs for long-term commitments, and cost estimates With these tools and services with implementation, companies can optimize costs, allocate resources more efficiently, and run their businesses more cost-effectively.
Additionally, cloud infrastructure reduces the operational costs associated with maintenance, upgrades, and support, as these responsibilities are usually handled by a cloud provider this allows organizations to divert resources and focus on core business objectives rather than IT management services.
Integration with Existing Systems
Integrating cloud services with your current systems is an important part of using cloud technology well. Many companies have already spent a lot of money on their own systems and software, so it’s crucial to make sure everything works together smoothly when you start using cloud services.
One way to do this is by using hybrid cloud solutions. This means you keep some of your stuff on your own systems and use cloud services for things like getting more space when you need it or being able to change things easily. Hybrid cloud setups help connect your own systems with the cloud so they can talk to each other and share information without any problems.
You can also use special tools like APIs (which help different software talk to each other), middleware (which helps connect different systems), and integration platforms. These tools make it easier for your systems to work together, whether they’re in the cloud or on your own servers. They make sure everything runs smoothly and your data stays consistent across all your systems.
Performance optimisation
Optimizing how well your cloud system works is really important to make sure you get the most out of it in terms of getting things done, using resources wisely, and saving money. Cloud systems have lots of options and ways to make them work better so you can do more without spending too much.
One way to make sure your cloud system performs well is by using the right amount of resources. This means giving your system enough power and space based on what you’re doing, so you don’t waste resources or run out when you need them. Cloud providers have tools to help you keep an eye on how your system is doing and make changes to save money and make things work faster.
Another way to improve performance is by using automation tools. These tools help you do things automatically without needing someone to do them manually every time. This makes things run smoother, saves time, and makes sure everything works the same way every time.
In summary, using cloud systems well means planning carefully, working together, and doing things in a smart way. By moving to the cloud, connecting with your existing systems, and making sure everything runs smoothly, you can use technology better, be more flexible, and stay competitive in today’s digital world.
AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are fancy ways of saying smart computer programs that can learn and make decisions on their own. These technologies are changing how companies use data, automate work, and make choices.
Cloud infrastructure, which is like a giant computer system on the internet, is a perfect place for AI and ML. It’s big enough to handle lots of data and powerful enough to run these smart programs.
When AI and ML are combined with cloud systems, companies can do cool things like finding important information in big piles of data. For example, they can train these smart programs to spot trends, predict what might happen next, and make things run smoother in areas like money, health, selling stuff, and making things.
Using AI and ML in the cloud also means companies can make computers do boring tasks automatically, like answering customer questions or finding problems before they happen. This saves time and helps businesses work better.
From chatbots that talk to customers to systems that predict when machines need fixing, the possibilities with AI and ML in the cloud are endless. It’s like having super-smart helpers that make everything easier and faster.
Internet of Things (IoT) Integration
The Internet of Things (Io) is a big network of connected devices, sensors, and systems that talk to each other and share information over the Internet. Cloud infrastructure is like a big storage and processing center in the sky that helps manage this information
When we integrate IoT with cloud infrastructure, it means we connect all these smart devices and sensors to the cloud. this connection let us do things like getting relevant information from these devices, controlling them from afar, and making our processes work better.
For example, in big developed cities, we can use IoT sensors in things like traffic lights and buildings to collect data on how people move around, the air quality, and how much energy we are using. Then, we send this data to the cloud where it’s analyzed. This helps city planners make better decisions about things like where to put new roads or parks, and how to make the city more eco-friendly
Cloud-based IoT platforms are also great because they can grow and change easily. This is important because we’re using more and more smart devices every day in different industries like healthcare, farming, and making stuff. So, having a flexible system that can handle all this new tech is super helpful!
Blockchain Integration
Blockchain Technology best known as the Technology behind cryptocurrency like Bitcoin, is increasingly being used to enhance the security and transparency of cloud infrastructure. Blockchain Technology can help organizations Secure data valid and processes and mitigation risks associated with a centralized system.
In cloud infrastructure, blockchain integration can be utilized in various ways, such as securing data storage and transmission, verifying the integrity of software and firmware and updates, and enabling secure peer-to-peer transactions. For example, blockchain-based identity management systems can provide a more secure and efficient way to manage user authentication and access control in cloud environments.
Moreover, blockchain technology can enhance the transparency and auditability of cloud infrastructure by providing a tamper-proof record of all transactions and changes made to data and configurations. This can help organizations demonstrate compliance with regulatory requirements, enhance trust among stakeholders, and improve accountability in cloud-based systems.
In conclusion, leveraging advanced cloud services such as AI and ML, IoT integration, and blockchain technology offers organizations a multitude of opportunities to innovate, optimize processes, and enhance security in their cloud infrastructure. By harnessing the power of these technologies, organizations can unlock new insights, improve decision-making, and stay ahead of the curve in today’s rapidly evolving digital landscape.
Ensuring compliance and governance in cloud infrastructure is paramount for organizations operating in today’s regulatory environment. As businesses increasingly rely on cloud services for data storage, processing, and management, it’s essential to prioritize adherence to industry standards and regulations, maintain data integrity and privacy, and effectively manage risks associated with cloud infrastructure.
Regulatory Compliance
Following rules and laws is very important when managing a cloud system well. There are different rules like GDPR, HIPAA, PCI DSS, and SOC 2 that have strict requirements for handling data and keeping it safe.
First, organisation need to know what rules they must follow based on their industry, where they are, and what kind of data they use. For example, healthcare groups must follow HIPAA To protect patient information, while businesses dealing with payment cards need to be strict with PCI DSS rules.
Providers of the cloud also play a big role in following these rules. They often help certificates showing their follow the rules correctly. Organizations should choose providers with good complain programs and clear audits.
Inside the organization, clear rules and plans are needed to keep following the rules. This includes who can access the data, how data is kept safe, how long data is kept and what to do if there is a security problem.
Regular checks and evaluations are important to see if everything is following the rules properly. These checks help find any problems and fix them so that data stays protected and legal requirements are met.
Data Governance
Data governance is about keeping data safe, accurate, and following rules, especially in cloud setups. it is all about the rules, processes, and tools that control how data is collected, stored, used, and deleted.
In a cloud system strong data governance means protecting sensitive data stopping unauthorized access, and following the rules. This includes using tools to classify data, encrypt it control who can access it and prevent data leaks.
Organizations also need clear rules on how data is accessed, shared, and used to avoid breaches. Data governance should include checks, monitoring, and rules to make sure everyone follows the data rules and meets legal requirements.
Risk management
Managing risk in cloud infrastructure is very important for ensuring the safety and reliability of business operations. Cloud introduces various risks such as data breaches, service interruption, vendor dependency, and regulatory violations, which can lead to significant, financial, reputational, and legal consequences
To effectively handle these risks, organizations need to conduct risk assessments to identify potential threats, vulnerabilities, and impacts on their cloud infrastructure. This involves analyzing the security measures of cloud service providers, examining data protection controls, and pinpointing the weak spots in the infrastructure.
once risks are identified organizations should start to develop risk mitigation strategies and backup plans to address vulnerability and decrease the chances of adverse events. This will also include implementing security tools like firewalls, intrusion detection, and vulnerability scanners as well as backup and disaster recovery plans to ensure business continuity in case of destruction or data loss.
Once risks are identified, organizations should develop risk mitigation strategies and backup plans to address vulnerabilities and minimize the chances of adverse events. This may include implementing security tools like firewalls, intrusion detection systems, and vulnerability scanners, as well as establishing backup and disaster recovery plans to ensure business continuity in case of disruptions or data loss.
Moreover, organizations should regularly monitor and evaluate their cloud infrastructure for emerging threats and vulnerabilities, and update their risk management strategies accordingly. Staying informed about security updates, patches, and best practices recommended by cloud providers and experts is crucial for maintaining a secure cloud environment.
In precise, ensuring compliance and governance in cloud infrastructure requires a comprehensive approach that includes regulatory adherence, data governance, and risk management. By prioritizing compliance with industry standards, implementing strong data governance practices, and effectively managing risks, organizations can mitigate potential threats, safeguard sensitive information, and uphold the security and reliability of their cloud setups.
Implementing cloud infrastructure effectively necessitates meticulous planning, collaboration, and execution. By utilizing cloud migration strategies, integrating with existing systems, and optimizing performance, organizations can harness the full potential of cloud computing, driving innovation, agility, and competitiveness in the digital era.
Follow Me for regular Updates on LinkedIn; Twitter; Facebook & Instagram for all Technology Articles
View My other Blog posts Here
Join Us on GRK Connect @ Telegram; Discord & LinkedIn Groups for Discussions on Technology

Cyber Security Best Practices for Businesses: Protecting Your Assets in the Digital Age
The Internet is increasingly becoming a popular environment for business and investing in it requires proper measures taken to safeguard your assets.
Cyber Security Best Practices
Indeed, proactive measures against cyber-attacks make many firms shut down their operations in the digital age. Financial loss and loss of intellectual property, cyber terrorism, ransomwear, phishing, malware and data theft. Emails, credit card details, and even customer lists, intellectual property, even lists containing employee information are all vulnerable to hacking by someone interested. That is why there are hackers out there, always robbing or invading your treasures.
Cyber-criminals are on the prowl, and regardless of the scale of the business or the specific type of digital property, cybersecurity must be taken seriously by all organizations. To this end, this article focuses on the different threats, the importance of cybersecurity, preventing, measures, tools, and guidance that one ought to consider for the enhancement of cybersecurity and the shield of properties against internet vices.

This is the procedure that aims at stopping other people from accessing networks, technological devices, and even personal data without permission. Cybersecurity is also required to avoid loss in data due to cyber-terrorism for each individual, businessman or a governmental organization. The importance of cybersecurity has been fueled by the current advancement of technology in the society. It encompasses a host of protection measures to prevent the loss of data and deter potential cyber threats that result in its compromise and unavailability.
In general cybersecurity can be rightly understood that it is a process of minimizing data risks by implementing and applying means and tools that ensure trust in digital environment. In this regard, both cybersecurity and compliance with enhanced and accurate security systems should be high priorities in order to minimize threats of hacked cyber-world incidents and further negative implications of security breakage.
More than ever, it is crucial to protect our personal data and possessions that are stored through digital means.
In the present day, intuitive measures have to be taken to protect your investments from cyber threats. One can safeguard anything that can endanger one’s identity, financial status, or image, including money or other important documents. Some crucial elements of safeguarding assets from cybercriminals are as follows:Some crucial elements of safeguarding assets from cybercriminals are as follows:
Maintaining Financial and Personal Identity
Firstly, identity information and other financial details are the valuable resources that need protection. Due to this, fraudsters are in a position to acquire credit cards and other identity cards, reach various e-shops and even compromise the tax system through tax frauds. This may be due to inadequate password protection or the passwords being easily guessable; it is thus important for you to ensure that you use proper passwords, and where possible change them frequently in a bid to protect your data from such individuals.
First, ensure that your data is safe by protecting your identity through two-factor authentication, and second, ensure that you do not disclose your identity on the internet. However, please read the following tips on how you can protect yourself against financial fraud: Finally, you should never use your credit card or bank account on the internet using public wireless networks and ensure you review your credit card and bank statements for any suspicious activities frequently.
Safeguarding Your Company’s Resources
Everybody knows that being an owner of a business, you must do all that is possible to protect the businesses you own. Whether it is about eating, paying through a credit card, getting to know confidential information or about closing your business, hackers are capable of doing all this. To try to protect the business’ assets, one should set a complex and unique password and employ two-factor authentication. In addition to this, do use firewalls and antivirus software and ensure to update your software routinely to reduce the risks to your network. Training your employees to develop risk awareness and keep away from frauds as well as other risks can also be done.
So, here are the most effective tips to increase the level of cybersecurity sources investment:
To mitigate cybersecurity there are several measures that will be available for application in protecting the company’s assets. This is a process that has components such as firewalls, antivirus, intrusion detection among many others. Now, let us say we are considering cybersecurity, some of the factors that should not be dismissed include cost, convenience, and efficiency. Search for real-time detection or threat and other features, if any, if you are trying to find such solutions.
Regularly backup your data
Without a doubt, this is one of the most effective means to ensure your asset’s safety, following the creation of backup files. One of the best recommendations that you could make as per the best practices in using computers is to always have data backup in the cloud. It is also important that you should frequently run cross checks on your backup in order to enable your data to be retrieved from invasions within the shortest time possible.
To be effective serious incidents require a plan on how to respond to them when they occur.
Cybersecurity is essential for any business, which means they should have cybersecurity strategy for addressing cyber threats. Thus, establish protective and aggressive response measures outlining the steps needed to avoid and manage such occurrences in the future. Here are some things that you need to ensure in your organization: You should consider some factors when it comes to incident response strategy to ensure that it is working effectively as follows:
Following these tips will help you protect your belongings from corrupt individuals.
Types Of Cyber Threats
In the current world, information technology has become widespread, and therefore industries must employ cybersecurity strategies to prevent their data from being compromised. The effects of cyberattacks range from severe personal ramifications on one’s financial, reputational, and personal fronts. This is because the world of cyber threats cannot be left unknown to comprehend the category of risks at the same time learning how to protect the assets of the business from hackers. Typical cyberthreats and preventative measures are listed in the following list:
Malware
Malware is a sort of software designed to harm your computer system and communication system. Trojans, worms, viruses, and malware may form part of what it is. Several scenarios exist through which malware may penetrate a certain system; for instance, when a user opens an email with an unsafe link, downloads infected content or visits a specific website. Malware can be defended by regularly installing antivirus software, updating installed softwares, avoiding clicking links that seem suspicious or avoid downloading files from unapproved sources.
Phishing
Phishing is one kind of social engineering that aims to help an attacker obtain passwords, credit card numbers, and other personal data. The cyberthreat could be a pop up window saying something like free and easy money, an email, a message saying call the bank, any message saying that is from the banks or any official authority. In order to avoid phishing pointers, it is also important to avoid providing links or files from unknown sources. This is why one should make sure they select a robust password while protecting the account through two-factor authentication.
Distributed Denial of Services
One type of cyber oppression is called DDoS (Distributed Denial of Services) attack, where a network or website inundates with traffic and creates an impediment to access by legal users. One of the tools included in the attacker’s arsenal is botnet attacks that involve the establishment of control over computer networks. If you want to mitigate DDoS attacks you have to use a DDoS protection service, monitor input and output traffic and, most importantly, have a contingency plan for when everything goes wrong.
Insider Threats
The type of cyber threats that originate from within a firm are called insider threats. Whether acted with premeditation or not, the performers can negatively affect the financial report of the company and its image. It is a hazard since it involves partners or employees with a possibility of accessing personal details of individuals. To avoid insider threats, you should really focus on making security awareness training as a routine exercise, observe human behavior, and strictly regulate access.
MITM
This can be achieved by use of Man-in the Middle (MITM), which is an intrusion technique prevailing in computer networks and telecommunications that allow an attacker to eavesdrop on, intercept, and even influence the communication sessions between two parties. Apart from impersonating the user and gaining his/her identification data, the hacker may also alter the data and track conversations. To avoid using open Wi-Fi connections, it is recommended to apply secure connection like SLS/TLS to defend oneself from MITM attacks.
In this world of technological advancements, the threat of having data stolen by a cyber-threat could happen to any company. It is important that you act to protect your assets appropriately in this era. When it comes to possible cyber risks, and implementing these preventive measures you could decrease your likelihood of a cyber attack and protect your business.
Identify System Vulnerabilities
To many, identifying the points of weakness that the hackers will use to bring down your system is one of the most crucial steps in system security. Yet another important component of cyber security is called vulnerability assessment; this is an identification of the points of access to the system that can be potentially penetrated by an attacker. It requires scanning all the system components of the hardware as well as the software in an attempt to find out the weaknesses. And in this section, we will discuss how one can search for system vulnerability so that you can protect your property.
Perform a Vulnerability Analysis
One of the ways of identifying security loopholes in any system is through performing vulnerability scans. The vulnerability scan procedure involves searching for specific weaknesses in systems with the help of various programs. This is done at a software level and the program will tell one where it think is most at risk and with what level of risk.
Verify any penetrations
It means introducing an assault on your system to experience it firsthand In other words penetration testing means. From the above information it’s clear that penetration testing is more efficient than vulnerability scanning in terms of identifying flaws.
Verify Your Configurations
Actually, the configuration is often viewed as the most common cause of system openings. It is important to check that all your system settings are properly configured in the right level for the highest security measures. Here are the network configurations, users and system authorities, configured firewalls and network barriers.
Monitor your System
Some of the benefits that you are bound to derive from the implementation of monitoring include; Monitoring your system will enable you to note any activity that goes astray and that could be as a result of a vulnerability. In this case, every single traffic in the network, and the actions performed by users are recorded as logs. There might be limitations to theuseer access, monitoring systems, and other security measures.
If you don’t want to lose the resources of your business, you need to find out any regularity gaps. Just like an information security analyst, proper management is crucial for maintaining the safety and security of our system.
Best Practices for Cybersecurity
Securing computer systems, networking devices, servers, and hardware equipment is crucial to safeguarding information and data from unauthorized access.. As the number of cyber threats continues to grow day by day with increased complexity, it is crucial to follow some fundamental strategies that work.
Make a Secure Password
Implementing proper passwords enhancement also helps in the enhanced cybersecurity. Some common practices of creating passwords are as follows: passwords should contain letters in both upper and lower cases, numbers, and/or special characters. The password should not contain or suggest any identifiable information such as name, address, or date of birth. It can be such a headache; people do not repeat the same password when creating accounts with different platforms. To avoid hackers penetrating your details, it is advisable to change passwords frequently
Regularly Update Your Software
To correct these problem and vulnerabilities, Sometimes software has to be updated. It is critical to always update all the software to protect against such weaknesses despite the requirements to update security software only. Often it is necessary to ensure that the newest version of the software is installed, and this may be done if you allow the corresponding option of the automatic software updates.
Implement Multi-Factor Authentication
Another feature is the use of several factors in the identification process, so-called multi-factor authentication. Two factors of identity have to input during the login process for instance a password plus a token that is sent to a mobile device. A strong means of protecting your information from unauthorized accounts is through utilization of multi-factor authentication.
Set Up Antivirus Software
Antivirus software comes as a handy tool that helps one to recognize and delete config applications that are not effective and could be hazardous on a computer. A computer user should constantly update their AV software to protect their valuables from virus, malware, and other shad’ software.
Frequently Backup Your Data
For the data which can be regained in case of any risk from the cybercriminals or system mishap, making copies of the data is crucial. Data should be copied by the user to external hard drive or to a remote server through the internet. Ensure that you take a backup to ensure that the data could be retrieved in cases of cyber intrusion or data corruption.
Implement Firewalls
A Firewall is one of the most effective defense mechanisms that can ensure your network has protection against hackers. The operating system is also another significant component of the computer since it mediates between the computers and the internet. Firewalls restrict inbound traffic which is not desirable thanks to the approval of traffic only in your network only. Firewalls come in two varieties to safeguard your data: What is clear is that TV needs hardware and software. There are two forms of firewalls, the first category involves software and these can be installed directly into the computer while the second form of firewalls are in-built in routers and this are referred to as hardware firewalls.
Data Encryption
Encryption means to check a code to protect data from attacks such as hacking by unauthorized persons. The personal data and information regarding finance and trade both belonging to the client and Trend Micro as well as other forms of company asset are protected through encryption. There are several techniques present these are hashing and symmetric as well as asymmetric techniques. When it comes to the encryption tools that can be used to protect the information, there are popular products, including Bitlocker, 7-zip, and Veracrypt.
Virtual Private Network
Perhaps the most effective cybersecurity solutions for maintaining your anonymity and protecting your digital identity are VPN. To ensure that hackers do not monitor your movements online, this can mask the transmission of internet traffic and camouflage your IP address. As it stands, the internet contains many free and paid VPN services, and the number is growing more and more. There are providers such as Cyberghost, ExpressVPN, and NordVPN among others.
A cyber attack happens when hackers try to invade an organization’s computer systems without authorization to create maximum chaos. Regrettably, every organization is vulnerable to cyber attacks because it is simple for individuals to impersonate others online. This makes it important that every organization establishes measures that allows it to quickly respond to a cyber attack.
Once a cyber attack is observed, one must not delay, but take the necessary actions against his/her possession to reduce the level of risk. The following steps must be taken in the case of a cyberattack.
figuring out what kind of attack it is
The first step is to figure out what kind of strike it is. You can deal with it by looking for signs of an attack on your system, like slow network speeds and other things. You need to keep an eye out for anything that seems fishy, like illegal access and logins. As soon as you see that your assets are being attacked, you need to take steps to protect them.
Stopping an attack
As soon as you know what kind of attack it is, you need to act quickly to protect your assets from more damage. Systems that are affected might need to be shut down and networks might need to be removed. You should always change your password and other entry information so that someone else can’t get to your data. As a business owner, you should still tell your clients about the attacks and take steps to keep their info safe.
Get Your Data Back
Once the attack is over, the next step is to get the info back. One way to fix this is to reinstall the app and make a copy of the data. You should also keep the software and protection system up to date to stop attacks even more.
Cyberattacks can be dealt with in a number of ways, including:
Rent a protection company from a third party
Getting in touch with police
Make an incident statement
There are pros and cons to each of these choices. You should look over how you handle hacks to protect your assets from more damage.
Keeping your business safe online
These days, businesses focus more on digital tools. So, cybersecurity is important for keeping business resources safe. Cybersecurity is the process of keeping private data and a company’s good name safe. Businesses should care about safety for these reasons, and here are some ways to do it.
The data leak could do a lot of damage to the company’s image. People might stop trusting the business, which would be a terrible waste of time and money. Because of this, security problems can lead to bad press and more damage to a company’s name. So, to keep info safe from hackers, follow the best practices for cybersecurity.
Cybersecurity is a way for businesses to protect their valuables from being hacked. Lastly, make sure you follow the above cybersecurity steps to keep your info safe and ensure long-term success.
Last Thoughts
Businesses should put cybersecurity at the top of their list of priorities to keep their important online assets safe. Even though online threats change all the time, new holes will appear. To stop data breaches and deal with them when they happen, you need a good protection plan. Put up firewalls and antivirus software to protect yourself from hacking, and show your employees how to do the same.
Cyberattacks are less likely to happen if you keep your software up to date and get back any data you may have lost. Companies that want to protect their customers, business, and financial information should think about the above strategies and suggestions. Lastly, make sure that all business deals, no matter how big or small, have a strong foundation.
Follow Me for regular Updates on LinkedIn; Twitter; Facebook & Instagram for all Technology Articles
View My other Blog posts Here
Join Us on GRK Connect @ Telegram; Discord & LinkedIn Groups for Discussions on Technology
Top Monetization Websites

Top Monetization Websites
Monetization websites have gained significant popularity in recent years as digital entrepreneurs and content creators seek avenues to generate revenue online. In this digital era, people always look for making money from digital platforms. Monetization websites are becoming more popular day by day. However, this platform helps individuals to earn money from their content, skills, and online activities. This article will cover over 30 monetization websites. These platforms offer various methods for individuals and businesses to monetize their content, skills, and online presence. In this article, we will explore the top 100+ monetization websites and provide detailed information about each platform, outlining their key features, monetization methods, and suitability for different types of users.
Google Adsense Monetization

- Google AdSense: Google AdSense is a program run by Google where the website owners and bloggers are offered to display ads on their websites. When the viewers click on view these ads,the individuals can earn money. AdSense works well for all types of content creators. AdSense is easy to use. It also has many options for customization.These advertisements are administered, sorted, and maintained by Google.This program also operates on HTTP cookies. Google uses its technology to serve advertisements based on website content, the user’s geographical location, and other factors.
- Ezoic: Ezoic is a digital platform which helps you place ads on your website in best spots to get maximum earnings. It is also an award-winning technology partner for digital publishers and content creators. This platform leverages artificial intelligence to comprehensively analyze the behaviors of both web visitors and advertisers. However, It tries out different layouts and setups, giving you useful insights to help you make more money. Ezoic is built for everyone, that is ,from bloggers to major brands. It is the first platform built to provide the value of large teams and modern data science without any of the overhead or complexity associated with managing these sophisticated systems. Ezoic was also the recipient of the Google Business Innovation Award.
- Media.net : Media.net is a top advertising network that shows targeted ads. They offer high-quality ads as well as competitive revenue sharing, making it a well built alternative to AdSense. Media.net also has the industry’s first server-side header bidding platform that maximizes yield without compromising the user experience. Their offerings incorporate proprietary machine learning technology, sophisticated data processing, and detailed analytics capabilities to successfully target internet users. By revenue, Media.net is the second-largest contextual advertising business worldwide.
- Infolinks: It is an in-text advertising platform. It converts selected keywords within your content into ad links. Since it has various ad formats, Infolinks is famous among thousands of publishers. Advertisers use Infolinks’ intent-driven ads to reach the right audience and deliver ads in real-time when users are most engaged and relevant. The secret to the success of Infolinks’ advanced ad solutions is the relevance, targeting and unprecedented viewability rates of 90%. They work with thousands of advertisers such as Nike, Virgin Airlines, Target, and Netflix to deliver nearly 1.5 billion monthly ad views.
- PropellerAds: PropellerAds comes up with a variety of ad formats. Pop-under, push notifications and native ads are some of them. PropellerAds assists the Publishers to monetize their websites, mobile apps, or their browser extensions. They provide access to unique traffic sources and Al-based ad-serving / optimization tools for media buyers, agencies, brand owners, and affiliate marketers.
- This includes advanced Demographic and Interests Targeting to find matching audiences, CPA Goal pricing model for automatic bidding and optimization, efficient ad formats (Push, In-Page Push, Interstitial, Popunder) with unique templates for customization,
- Revcontent: Revcontent is a leading content marketing and native advertising platform that leverages lightweight, customizable technology to empower the web’s leading publishers and marketers to reach and exceed their revenue, engagement and growth goals. Revcontent is also native advertising platform. It focusses on delivering high-quality content recommendations to engage users. Revcontent’s personalized ad widgets deliver a smooth interaction with your website while monetizing your audience.
- Taboola: Taboola is a top content discovery and native advertising platform which can provide personalized content to publishers recommendations to their readers which makes it capable of monetization strategy. The company’s platform, powered by artificial intelligence, is used by digital properties, including websites, devices and mobile apps, to drive monetization and user engagement. Taboola has long-term partnerships with some of the top digital properties in the world, including CNBC, NBC News, Business Insider, The Independent and El Mundo.
- Adversal: Adversal, which is a CPM-based advertising network, provides competitive pricing to the publishers. They have various ad formats and advanced targeting options and hence are a great choice for monetizing one’s website.
- Sovrn //Commerce: Sovrn //Commerce previously known as VigLink is a perfect affiliate marketing platform. It serves the purpose of automatically converting product links into the so-called affiliate links. When individuals use these links, publishers earn a commission.Sovrn Commerce empowers publishers and content creators to effortlessly generate income through monetized affiliate links. With their user-friendly extension, you can seamlessly convert any product page into a shareable link, allowing one to earn commissions from clicks or sales resulting from that link.
- Skimlinks: Skimlinks is an affiliate marketing platform. They help publishers to monetize their content. It is done through affiliate links. It can also automatically convert product mentions into affiliate links which allows the publishers to earn commissions from relevant purchases. Skimlinks powers commerce content strategies for publishers. They are the world’s largest commerce content monetisation platform, it helps grow a revenue stream that can contribute as much as a quarter of a publisher’s overall revenue, which enables publishers to be less dependent on advertising. Its technology automatically earns publishers a share of sales they drive through product links in commerce-related content created by editors. The platform is a one stop solution providing the technology and the data to start, grow and successfully scale a content commerce strategy across desktop, tablet and mobile.
- Adsterra: Adsterra, known for its broad range of advertising network, offers various ad formats including pop-ups, banners, push notifications, along with interstitial advertisements. They have a 3-level security system, many flexible ad inventories, and industry’s best managers and support. Comprehensive targeting options are also available. Adsterra has been a choice for publishers because of its competitive pricing. Malware is strictly prohibited, along with redirects, unsolicited downloads, and virus alerts.
- Bidvertiser: Bidvertiser is an advertising network. Their main Focus is on technology, optimization and automation. It permits the publishers to display text advertisements, banner ads, native ads, and programmatic XML on their websites. They are also efficient in Real-time bidding and optimization. These features help to maximize the revenue of the same. Bidvertiser operates on a pay-per-click (PPC) model, where advertisers bid for placement in publisher websites’ ad slots. This dynamic auction-based system ensures that ads are displayed to the most relevant audience, maximizing both advertisers’ ROI and publishers’ earnings.
- Revive Adserver: Revive Adserver is a free open-source ad serving system that allows the publishers to serve ads on their websites. They have advanced targeting options and tracking capabilities. Also, they offer flexibility for revenue generation. They even define rules for delivery of campaigns and ads, including frequency capping, URL targeting, geo-targeting. And then Track campaign performance, including impressions, clicks, click-through rates, conversion rates, revenue, eCPM, and conversion details, like basket value and number of items purchased.
- AdRecover: AdRecover permits the publishers to regain revenue from ad-block users. This is done by displaying non-intrusive ads. AdRecover gives backup revenue stream while maintaining a positive user experience. AdRecover is a user-friendly solution to recover lost revenue due to adblocked traffic. AdRecover never compromises the user experience, creating a win-win situation for the visitors as well as the publishers. AdRecover educates the users about how banner ads help keep the world’s information free, accessible and the editorial unbiased. Users have an option to opt-out and report when they don’t like certain ads, on which we ensure prompt action.
- BuySellAds: This usually is a marketplace connecting publishers and advertisers. BuySellAds helps publishers to sell ad space directly to interested advertisers. They also render control over pricing and deals.Their tools, and services help marketers easily reach their target audience with contextual advertising, and publishers monetize their websites, newsletters, and podcasts. Specializes in cross-channel advertising, self-serve advertising, native advertising, sponsored content, email advertising, podcast advertising, display advertising, newsletter sponsorships.
- Adbuff: Adbuff is an ad network that focuses on high-quality ads. They are primarily centered on premium publishers. Adbuff is a platform for monetization having competitive CPM rates and real-time bidding. They help brands maximize their marketing ROI and make them more Memorable, Impactful and Profitable. They specialize in Facebook Ads, Instagram Ads, E-commerce Strategy, Google Ads, Amazon Ads, Performance Creatives, Shopify, Shopify App.
- AdMaven: AdMaven is mastered in pop-unders, push notifications, and also interstitial ads. They have high CPM rates, advanced targeting options, and a user-friendly interface. Hence, it is popular among the publishers. AdMaven is constantly building an engine which yields an increased revenue for publishers, while enabling advertisers to get high performance and vast distribution for their ad budgets.
- Adcash: Adcash which is a global online advertising platform, offering various ad formats like native ads, push notifications, and interstitial ads. They also have advanced targeting, real-time reporting. And its competitive CPM rates make it a decent choice for publishers. Ad inventories are uniquely optimized and placed according to the campaign’s targeting as well as the website’s individual ad compliance requirements, and vice versa. Maximum exposure is obtained on a wide variety of sites for advertisers to broadcast their offers to the widest possible audience.
- Advertise.com: Advertise.com is an online advertising platform. They also have various ad formats, including display ads, pop-ups, and native ads. It helps publishers with competitive rates and also advanced targeting options. They provide advertisers with high-quality exclusive traffic that performs and yields high ROI. Using our patented Click Shield click scoring technology, Advertise.com guarantees high-quality traffic. And also provide advertisers with quality traffic that converts, and publishers with competitive listings that yield high revenues. Using our patented Click Shield fraud protection software, Advertise.com guarantees high-quality traffic for both advertisers and publishers.
- Adverticum: Adverticum is an ad network which focuses on Central and Eastern European markets and offers various ad formats along with targeting options for publishers in those regions. The development of Adverticum AdServer works out by harmonizing global market trends and local client needs. Adverticum is engaged in providing great product support and in fulfilling unique needs of its clients flexibly.
- Adverty: Adverty is an in-game advertising platform. Also enables publishers to monetize their games. It includes non-intrusive ad placements that offer immersive and interactive ad experiences. It enables new gaming revenue streams for developers and empowers advertisers to reach uniquely engaged audiences. Adverty delivers spectacular In-Play ads to connect brands and people through its revolutionary and multi-patented technology built for VR/AR and mobile games. The platform offers programmatic video and display ad inventory at scale and allows content creators to monetise the complete experience with unobtrusive, easy-to-integrate, immersive ads.
- Adzerk: Adzerk is an ad serving platform that allows publishers to manage and optimize their ad inventory. It provides advanced targeting options and real-time reporting. Adzerk is “ad serving as an API”, a collection of products that enable developers to build native ads and integrate advertising into their properties.
- Adstargets: Adstargets is a self-serve advertising platform offering various ad formats, including native ads, pop-ups, and banners. Advanced targeting options and real-time analytics help optimize monetization.
- Affiliate Window: Affiliate Window as the name suggests, is an affiliate marketing network that binds the advertisers and publishers. It provides a variety of affiliate programs. And also helps publishers with advanced tracking and reporting features. Affiliate Window is a global performance marketing network with an innovative and ethical approach to performance marketing.
- Adkernel: Adkernel is an ad serving platform. It offers real-time bidding and optimization features for systematic monetization. Adkernel helps publishers with advanced ad management capabilities. They offer Programmatic Display & Video White-label Ad Serving Solution, Programmatic White-label Media-buying Platform (DSP), Server Side Header Bidding platform (prebid compatible), Variety optimization and analytic tools. The company’s industry-leading role provides enterprise-class solutions for pay-per-click, display and video, mobile and desktop markets.
- AdMantX: AdMantX which is an AI-powered advertising platform that provides advanced targeting and ad verification capabilities to publishers. It presents high-quality ads and personalized support. They specialize in Semantic Targeting, Contextual Advertising, Semantic Technology, Natural Language Processing, Audience Targeting, Artificial Intelligence, Advanced Profiling Services. ADmantX provides contextual analysis and data, offering a cookie-less solution for publishers and advertisers to develop online advertising.
- Adperio: Adperio is a performance-based advertising network that concentrates on mobile app monetization. Their platform provides various ad formats and targeting options for publishers. This leads to maximizing their revenue potential. Adperio, who is now Perform[cb], offers strategic plans tailored to meet their clients’ specific marketing goals. Perform[cb] is the pioneer of performance marketing and uniquely positioned to lead this space based on brand trust, team experience, compliance best practices and technological innovation.
- AdPushup: This is a revenue optimization platform that empowers the publishers to increase their ad revenue. This is done by automating A/B testing. It also has strategic ad layout optimization. They help web publishers grow their advertising revenue by using cutting-edge technology, premium demand partnerships.
- AdRiver: AdRiver is an ad serving platform. They provide advanced targeting options. It is the real-time reporting that enables publishers to manage and deliver ads on their websites. They are also leading Mobile Out of Home providers in Europe. AdRiver brings exclusive tech solutions to brands to guarantee them transparency and efficiency in their campaigns.
- Adstir: Adstir is a mobile advertising platform that has a wide range of ad formats, including banner ads, interstitial ads, and also rewarded videos. Adstir helps publishers with powerful targeting options and real-time analytics.Through their PMP marketplace, they deliver high-priced and premium ads. They do CPM evaluation and optimization from a fair perspective on the basis of the number of impressions counted by Ad network.
- AdSupply: AdSupply is a digital marketing company that focuses on delivering visible CPM advertising. They offer innovative ad formats and targeting options for publishers looking to monetize their audience. AdSupply creates patented, world-class ad tech that delivers viewable, high impact ad formats for brands, agencies and publishers looking to maximize Return of investment. They automatically redirect traffic in case they detect that there are no available ads from the ad network to another network.
- Adtelligent: Adtelligent is an advertising technology company that helps publishers with advanced ad serving. They also provide monetization solutions to publishers. It offers various ad formats and optimization features. They also specialize in Video Advertising, VAST/VPAID Compliant Player, Video Ad Marketplace, Header Bidding Wrapper Programmatic Buying, Ad Serving. Display Advertising, Native Advertising, Header Bidding, Banner Advertising.
- Adthink: Adthink, an advertising network, provides varieties of advertising formats, encompassing display ads, pop-unders, and also native ads. They help publishers with competitive rates and targeting options. They also cater to a spectrum of promotional needs to customers. Adthink addresses the B2C market by developing a global digital and physical distribution platform and the B2B market by providing advertisers with its trading desk and affiliate platform to develop their customer acquisition. With its proprietary adtech solution AdAccess, media publishers can optimize and multiply their revenue channels.
- AdTiming: AdTiming known as a global mobile advertising platform, offering a wide range of ad types, such as interstitial ads, rewarded videos, and native ads. It empowers publishers with real-time information and advanced targeting choices that can lead to the enhancement of their advertising strategy.They cater to e-commerce, games, utilities and social applications. It is a comprehensive supply chain from advertisement to monetization.
- AdTradr: AdTradr which is known for its programmatic advertising, bridges the gap between publishers and advertisers. And also advanced targeting choices. Its aim is to make the digital advertising space a healthier and more efficient landscape. Alternatives and possible competitors to AdTrader include Amura Marketing Technologies and Embold.
Follow Me for regular Updates on LinkedIn; Twitter; Facebook & Instagram for all Technology Articles
View My other Blog posts Here
Join Us on GRK Connect @ Telegram; Discord & LinkedIn Groups for Discussions on Technology

The Ever-Expanding Frontier: Securing the Wild West of the IoT
The Internet of Things (IoT) has emerged as an evolutionary force, reforming industries and everyday life in the digital era. With this technical breakthrough comes a new frontier, similar to the Wild West, where security concerns are paramount. While the businesses undertake digital transformation plans, the need to secure the expanding realm of IoT devices becomes the prime factor. The internet of things, or IoT, is a network of interrelated devices that connect and exchange data with other IoT devices and the cloud. IoT devices are typically embedded with technology such as sensors and software and can include mechanical and digital machines and consumer objects.
Increasingly, organizations in a variety of industries are using IoT to operate more efficiently, deliver enhanced customer service, improve decision-making and increase the value of the business. With IoT, data is transferable over a network without requiring human-to-human or human-to-computer interactions. Computer Engineers have been adding sensors and processors to everyday objects since the 90s. However, progress was initially slow because the chips were big and bulky. Low power computer chips called RFID tags were first used to track expensive equipment. As computing devices shrank in size, these chips also became smaller, faster, and smarter over time.
Thanks to the advent of inexpensive computer chips and high bandwidth telecommunication, we now have billions of devices connected to the internet. This means everyday devices like toothbrushes, vacuums, cars, and machines can use sensors to collect data and respond intelligently to users. This article is about the challenges as well as strategies for securing the Wild West of the Internet of Things.
Internet of Things (IoT)
The Rise of IoT in Digital Transformation Strategies:
Digital transformation strategies have become recalibrated for businesses to stay in today’s competing dynamic market. At the heart of this transformation lies IoT, a network of interconnected devices that communicate and share data. From smart homes and wearable devices to industrial machinery and smart cities, IoT applications are diverse and far-reaching. Despite being a critical element in digital transformation, IoT is often overlooked when businesses are laying out their strategies for digital innovation. However, the fast spread of IoT devices has overtaken the development of security measures, leaving them vulnerable to cyber assaults.
As more devices become interconnected, leading to the expansion of the attack surface, it exposes critical infrastructure and sensitive data to potential compromise.IoT devices share the sensor data they collect by connecting to an IoT gateway, which acts as a central hub where IoT devices can send data. Before the data is shared, it can also be sent to an edge device where that data is analyzed locally. Analyzing data locally reduces the volume of data sent to the cloud, which minimizes bandwidth consumption.
Sometimes, these devices communicate with other related devices and act on the information they get from one another. The devices do most of the work without human intervention, although people can interact with the devices — for example, to set them up, give them instructions or access the data. The connectivity, networking and communication protocols used with these web-enabled devices largely depend on the specific IoT applications deployed.
Challenges on the Digital Frontier are:
The challenges include: Increase in the attack surface as the number of connected devices grows. As more information is shared between devices, the potential for a hacker to steal confidential information increases. Also Makes device management challenging as the number of IoT devices increases. Organizations might eventually have to deal with a massive number of IoT devices, and collecting and managing the data from all those devices could be challenging. It Has the potential to corrupt other connected devices if there’s a bug in the system. TheyIncreases compatibility issues between devices, as there’s no international standard of compatibility for IoT. This makes it difficult for devices from different manufacturers to communicate with each other. The others are as follows:
Weak Authentication and Passwords: Many IoT devices ship with flimsy, pre-set credentials or simple password protection. A great example of this is the equivalent of leaving your saloon door wide open with a welcome sign for any digital outlaw. Hackers can easily exploit these vulnerabilities to gain control of devices and launch attacks on connected networks.
Data Privacy Concerns: IoT devices often collect vast amounts of personal data, from our daily routines. Many IoT devices are vulnerable to hackers and other cyberthreats, which can compromise the security and privacy of sensitive data. IoT devices can also collect vast amounts of personal data, raising concerns about privacy and data protection. Even our intimate health information. This data, if not protected, becomes a goldmine for venomous actors, leading to identity theft, targeted advertising, and can even lead to blackmailing.
Lack of Standardization: The diverse landscape of IoT devices, with abundant manufacturers and protocols, hinders a unified approach to security systems. Imagine horses, carriages, and spaceships trying to navigate the same dusty trail – there’s bound to be a collision if everyone follows their own rules by themselves.
Outdated Firmware and Patch Management: Many IoT devices have infrequent or nonexistent firmware updates, leaving them vulnerable to known exploits. It’s like riding a stagecoach riddled with bullet holes, hoping it won’t fall apart on the next bandit ambush. Outdated or insecurely built software creates gaps in this fence, making it easier for attackers to infiltrate systems and steal sensitive data, like credit card information. Patch management helps to strengthen this fence, ensuring its integrity and reducing the risk of a data breach.
Physical Tampering and Inaccessibility: Some IoT devices lack basic physical security measures, making them susceptible to tampering. Imagine a saloon safe built of cardboard – any determined varmint could break in and steal the loot.The security of IoT infrastructure should not be the exclusive responsibility of the cyber security team. Establish cooperation and shared responsibility between the cyber security team, operations and management team, and physical security team. Getting all three involved will ensure the best outcome.Remove any connectivity hardware—optical ports, radios—that exist purely for development reasons.
Also, if it makes sense given the structure and purpose of the devices, consider removing all test points or disabling test access and otherwise secure devices from unauthorized digital access. Any sort of test or admin access is likely to be the target used by attackers. Ensure all devices are in operations mode and not accidentally left in default setup, reset or pairing modes. Additionally, embedded systems within critical infrastructure might be inaccessible for traditional security solutions.
Building a Secure Frontier Town:
Just like the Wild West eventually found its law and order, Here are some key approaches to mitigate IoT security risks :
Strong Authentication and Encryption:It is widely known that users often do not take the extra step of changing the default username and password of their IoT device, thus leaving it completely vulnerable to password-guessing and cracking attacks like credential stuffing, brute-forcing, dictionary-based guessing, masked or rule-based guessing, and even using the help of trained neural networks to generate thousands of highly plausible guesses. Implementing multi-factor authentication and robust encryption protocols (like WPA3) strengthens the gates of the digital town, making it harder for outlaws to break through.
Data Minimization and Privacy Controls: Implementing the principle of “least privilege” which says that Principle in computer security that every module must be able to access only the information and resources that are necessary for its legitimate purpose and giving users granular control over data collection and usage empowers them to protect their digital nuggets.
Standardization and Open Platforms: Promoting industry-wide standards and open platforms fosters collaboration and creates a shared set of security rules, akin to a town sheriff uniting different factions.
Secure Firmware Updates and Patch Management: Patch management is the process of applying updates to software, drivers, and firmware to protect against vulnerabilities. Effective patch management also helps ensure the best operating performance of systems, boosting productivity. Establishing a system for regular and automatic firmware updates ensures the townsfolk are always armed with the latest defensive measures against evolving threats.
Physical Security and Remote Management: Proper (sufficient) security controls must be implemented at the web, software application, and OS or firmware level to ensure the best possible protection of security and privacy at each layer of an IoT device, but given the fact that these devices are often characterized by their restricted memory capacity, low energy, and limited processing power, it is often quite challenging to properly implement sufficient security measures in IoT devices as their hardware and subsequent software limitations pose a huge barrier for software developers while implementing core functionalities of the device.
Implementing tamper-proof hardware and remote access controls, akin to a fortified bank vault, makes it harder for physical attacks and easier to monitor and manage security remotely.
Beyond the Lone Ranger:
Securing the IoT frontier requires a collaborative and collective effort. Manufacturers need to prioritize security by design, consumers should be attentive about choosing secure devices and practicing safe usage habits, and also governments must play a role in fostering regulatory frameworks and promoting best practices. All these mentioned above should go hand in hand. By working together, we can transform the Wild West of the IoT into a thriving, secure community, where innovation multiplies with peace of mind. Remember, in the digital frontier, an ounce of prevention is worth a pound of cure – let’s build a future where connected devices empower us, not put us in danger.
Implement Robust Authentication and Encryption:
Strong authentication mechanisms play a crucial role in preventing unauthorized access to IoT devices. Multi-factor authentication, requiring users to provide multiple forms of verification, adds an extra layer of security beyond traditional passwords and systems. Additionally, certificate-based authentication leverages cryptographic certificates to check the identity of devices and users, ensuring only trusted entities can access sensitive data or control IoT devices.
And hence, encryption protocols such as SSL/TLS should be employed to safeguard data both in transit and at rest. Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols ( Secure Sockets Layer (SSL) is a security protocol that provides privacy, authentication, and integrity to Internet communications. SSL eventually evolved into Transport Layer Security (TLS) ) encrypt data communications between IoT devices and servers, preventing eavesdropping and data tampering by malicious actors. By implementing robust authentication and encryption measures, organizations can significantly enhance the security posture of their IoT deployments.
Regular Security Updates and Patch Management:
Manufacturers should prioritize regular security updates and patch management to address known vulnerabilities and mitigate emerging threats in Iot. Software vulnerabilities are frequently discovered in IoT devices, exposing them to potential exploitation by cybercriminals. Automated update mechanisms streamline the process of deploying patches, ensuring timely protection against newly identified security flaws. By promptly addressing vulnerabilities through regular updates, manufacturers can reduce the risk of IoT devices being compromised and prevent them from becoming entry points for cyber attacks.
Effective patch management is essential to maintaining the security and integrity of IoT ecosystems, safeguarding both user data and critical infrastructure. Also Effective patch management is a systematic and repeatable patch distribution process for closing IT system vulnerabilities in an enterprise. It involves pervasive system updates, including any or all the following: drivers, operating systems, scripts, applications, or data files.
Network Segmentation and Access Control:
Segmenting IoT devices into distinct network zones based on their function and security requirements is essential for minimizing the impact of potential breaches. By partitioning the network into separate segments, organizations can contain security incidents and prevent lateral movement by cyber attackers. Implementing access control policies based on the principle of least privilege ensures that only authorized users and devices have access to specific resources and functionalities. By restricting access to IoT devices and services based on predefined rules, organizations can reduce the attack surface and mitigate the risk of unauthorized access.
Network segmentation and access control measures are critical components of a comprehensive IoT security strategy, enabling organizations to proactively defend against cyber threats. Network micro-segmentation enables isolation of less-capable devices at the network layer, either behind a gateway or on a discrete network segment. Network segmentation leverages an EVPN-VXLAN architecture that supports a highly scalable and agile environment while maintaining the security and performance requirements needed to protect users and IoT devices.
Privacy by Design:
Privacy should be integrated into the design and development of IoT solutions from the outset to protect user data and build trust with consumers. Privacy-enhancing technologies such as anonymization and data minimization help mitigate privacy risks associated with IoT deployments. Anonymization techniques strip personally identifiable information from data collected by IoT devices, preserving user anonymity and confidentiality. Data minimization (Data minimisation means collecting the minimum amount of personal data that you need to deliver an individual element of your service.
It means you cannot collect more data than you need to provide the elements of a service the child actually wants to use) practices limit the collection and retention of sensitive information to the minimum necessary for the intended purpose, reducing the risk of unauthorized access and misuse. By adopting privacy by design principles, organizations can demonstrate their commitment to protecting user privacy and comply with regulatory requirements governing data protection.
Continuous Monitoring and Threat Detection:
Implementing real-time monitoring solutions and anomaly detection algorithms is essential for detecting suspicious behavior and potential security incidents in IoT environments. Continuous monitoring of network traffic, device activity, and system logs allows organizations to identify anomalies indicative of unauthorized access or malicious activity. Anomaly detection algorithms analyze patterns and deviations from normal behavior, alerting security teams to potential security threats in real-time. Rapid incident response mechanisms should be in place to contain and mitigate the impact of security breaches, minimizing downtime and data loss.
By maintaining continuous vigilance and proactive threat detection capabilities, organizations can effectively defend against evolving cyber threats and protect their IoT infrastructure from exploitation. By implementing these comprehensive strategies, businesses can significantly enhance the security of their IoT systems. This proactive approach helps to mitigate the inherent risks associated with the rapidly growing landscape of the Internet of Things. By doing so, companies can protect their valuable data and maintain the integrity of their connected devices, ensuring a safer and more resilient technological environment.
Conclusion:
Securing the Wild West of the Internet of Things is a complex and ongoing challenge that requires concerted efforts from industry stakeholders, policymakers, and cybersecurity professionals. By adopting proactive security measures and adhering to best practices, businesses can navigate the IoT landscape safely and reap the benefits of digital transformation without compromising security and privacy. As the frontier of IoT continues to expand, vigilance and innovation will be key to taming the Wild West of the digital age.IoT devices are increasingly being used by individuals and across the enterprise. They are not only here to stay, but proliferating exponentially in more and more forms. The result is increasing complexity, which hampers efforts to manage IoT systems security successfully.
IoT security challenges range from deflecting malicious insiders to defending against nation-state attacks. Because of the inherent vulnerability of IoT devices and the scale of their deployment, attacks continue to grow in scale and scope. Securing IoT devices is well worth the investment despite the IoT security challenges. The value realized with IoT devices can only be increased with enhanced security to be on par with other technology. It will mitigate risks and increase the rewards.
Follow Me for regular Updates on LinkedIn; Twitter; Facebook & Instagram for all Technology Articles
View My other Blog posts Here
Join Us on GRK Connect @ Telegram; Discord & LinkedIn Groups for Discussions on Technology

Cloud Computing Security Best Practices and Considerations: Safeguarding Your Digital Assets
Cloud Computing Security Best Practices: An individual is supposed to protect his/her digital assets in the same way as physical ones are protected.
Introduction:
Cloud computing presents many opportunities for corporations in terms of the scale, cost, and accessibility of computer resources. However, due to the heavy dependence on cloud services, how they protect data is an issue that deserves utmost attention. To avoid compromise of data and applications in the cloud, organizations have to use at least proper practices as well as consider several factors. To get you up to speed with cloud computing security measures, this extensive article covers the key guide on cloud computing security to enable businesses to reduce risks and ensure data confidentiality, integrity, as well as availability.

Data Encryption:
The Importance of Encryption
We start with protection of data through encryption as an integral preventive mechanism against threats in cloud environments. It is the process through which information is transformed to a mode that cannot be understood without a decryption tool. This makes certain that even when the data is intercepted or retrieved from the system by malicious users, they cannot comprehend or retrieve the data.
Best Practices for Data Encryption
Furthermore, data has been receiving more attention recently, which is understandable given its significance for all types of organizations and businesses, from startups to established ones. Utilizing data encryption technologies is one method of protecting data. Although there are many ways to secure data, the following guidelines suggest encrypting data:
Encrypt Data at Rest and in Transit: To prevent unwanted access, data must be continuously encrypted while it is stored on the cloud (also called “data at rest”) and while it travels between locations (sometimes called “data in transit”).This helps to avoid infringement during both storage and transmission of interfaced data communications.
Use Strong Encryption Algorithms: Ensure that data is encrypted using a combination of advanced algorithms such as the Advanced Encryption Standard-256 for data in storage, and Transport Layer Security 1. Data in transit, in contrast, could generally be kept at 2 or higher. These standards are also popular in their security measure.
Secure Key Management: Maintaining security and privacy of keys and Key management is another pivotal issue as vital as encryption. Hardware security modules (HSM) are designed to hold the encryption keys while cloud key management services (KMS) offer the process as a service. Additional measures that can be observed is that key rotation polices actually add layers to security.
End-to-End Encryption: Protect the data by designing mechanisms that encipher the data at the stage of creation and afterwards during storage and disposal. This includes data backup or storing data in archives.
Identity management solutions in cloud computing
Identity and Access Management or Identity and Access Control or simply IAM is one of the key aspects that are relevant while considering the cloud security. This involves access mechanisms, such as identities of the user and resources and tools that are used to authenticate the same. The way IAM is done ensures that any individual that tries to access data or any application that is reserved for certain users only is locked out.
Best Practices for IAM
Implement Strong Password Policies: The qualitative studies were also based on the following measures: Conduct compliance audits regularly with strict password legislation to ensure that users choose difficult passwords and change them often. Avoid password sameness and promote passphrase.
Multi-Factor Authentication (MFA): Therefore it is recommendable to employ MFA to enhance security by adding another level of barrier to access one’s account. It entails the use of two or more verification factors to be used when preparing to access the platform to minimize incidences of a breach in the credentials.
Network Segmentation: Segment the network into smaller subnets that are not interconnected such as a DMZ or demilitarized space. This approach has the possibility of risks and is really good in securing some valuable assets.
Use intrusion detection and prevention systems (IDS/IPS) to periodically check the network for any unusual behavior and stop it before it has a chance to become a serious danger.
Frequent observation of the network: Watch out for unusual activity at all times to possibly uncover security lapses and intrusions: Employ event management and security information to keep an eye on dangers in real time.
Vulnerability Assessments: Carry out periodic security audit to uncover possibly existing security weaknesses. Patch learned his or her mistakes in terms of weaknesses identification so that the he or she did not give a chance to the attacker to take advantage.
Data Backup and Disaster Recovery
A backup can be defined as the preservation of data and information which takes various forms and is classified depending on the form it takes into several categories as follows;
Ensuring Business Continuity
Business continuity is critical and so is the reliability of cloud-based backup and disaster recovery programs. It is beneficial to periodically copy and store essential data, as well as distribute Copies of such data across different geographical locations or availability zones to minimize data loss and increase the speed of restoring data.
There are several special best practices for data backup and disaster recovery including:
Regular Backups: Back up frequently accessed data and application data to ensure that recent data can be reproduced in case of data loss. There are number automated backup solutions that can help in this process.
Geographic Redundancy: Location backups in different geographical area or in different availability zones will help in handling the regional calamities and for provision of data access.
Testing Restore Processes: Perform some disaster recoveries from time to time, to confirm that backup can be recovered easily. This confirms that the shied data backups are complete and reliable.
Recovery Time Objectives (RTO): Set RTOs to identify the actual tolerance time for essential systems and processes outage. It is important that the organizations take the following steps to achieve the set goals in the realization of these objectives.
Recovery Point Objectives (RPO): Define RTOs to identify the maximum timeframe of business disruption to put into practice the acceptable data loss. To achieve this, ensure the back-up you schedule meets the particular Recovery Point Objectives set to reduce data loss.
Security Patch Management
Security patch management is a vital component of any business or organization because the absence of proper security patch management leads to security breaches that affect the business or organization.
Best Practices for Security Patch Management
Automated Patch Management: Automate the process of patch and update management by installing appropriate tools that would help in popping up the patches and updates once released. It also minimizes human intervention hence; there is proper timing in updating the indices.
Vulnerability Scanning Tools: Continue your vulnerability scanning to discover such threats and patch management progression. A few checks in a day are highly essential to ensure that there is no penetrating security threat in the system.
Monitoring Security Advisories: As a user, ensure that you are up to date with the newest security notices from your OS and application developers and cloud solution partners. Seamlessly implement fixes for newly discovered vulnerabilities as it is critical to avoid compromising the system.
Patch Testing: To develop test patches first develop them in a staging environment before going to the actual production site. This makes it easier to ensure compatibility, and thus reduces the potential for interference or disruptions.
Incident Response and Monitoring
Preparing for Security Incidents
Relating to the need of every computer system to have an incident response, it has been established that every system must have the following; Using IDS, upgraded SIEM tools, and log monitoring solutions are the ways through which it is possible to detect threats as they occur in realtime.
This paper contains recommendations that can be followed when dealing with incidents and also the procedures that should be taken in reviewing the incidents.
Intrusion Detection Systems (IDS): On this level it is necessary to deploy IDS to monitor the traffic for any suspicious activity. There is also IDS intrusions which are capable to identify and notify security groups of the potential violations.
Security Information and Event Management (SIEM): Engage with SIEM when it is time to compile and parse as well as correlate security information which has been gotten from different points. SIEM allows for identifying adverse events in real-time and managing them through a single point of contact.
Log Monitoring Solutions: Begin practice of log usage monitoring and implement solutions for logs used in cloud resources. It helps in detecting outliers and suspicious activities of security flaws.
Establish a core team to handle security incidents and give them the authority to look into and address security concerns. This is known as the incident response team. It’s also critical that the right individuals are prepared to address the issue with the necessary training and tools.
Regular Security Drills: Ensure that institutions maintain regular security drills in their quest to enhance response to security threats. It is quite obvious that the flaws of the plan have to be pointed out and strengthened during the simulated exercises.
Evaluating Cloud Service Providers
Specifically, while choosing CSP, one has to pay attention to the security measures and standards that the CSP follows. The next step is to assess how well the provider meets various standards and requirements, for instance, being ISO 27001 certified, accredited with SOC 2, or following the provisions of the GDPR.
Security assessment of a cloud provider: Key issues and approaches
Compliance and Certifications: Thus, it is also important to ensure that the selected cloud provider meets all legal requirements and fulfills industry standards. Search for Service organization control SOC 2 type 2, ISO 27001, and General data protection regulation GDPR.
Security Practices and Policies: Consider security standards of the cloud provider. Make sure that they meet not only your organization’s security needs and standards, practices, and procedures.
Incident Response and Support: Rate the response to security incidents based on the selected cloud provider’s experience and approach. Make sure they have an efficient mechanism for managing security breaches and provide them with assistance in the worst-case scenario.
Data Privacy and Compliance
Ensuring Regulatory Compliance
There has been a significant concern over data protection and privacy, especially when data is stored and processed on cloud. Learn with legalities that pertain to your chosen trading sector and country or state policies that apply to your trade business.
Data Privacy Controls: Adopt the right measures to protect the privacy of data that is collected in the organization. This includes ensuring that the data gathered is anon, and encrypted in addition to applying access restrictions.
Data Retention Policies: Stipulate when information should be deleted or discarded to prevent the unnecessary storage or accumulation of data. Preserve information in accordance with policy and/or legal standards on recordkeeping and disposal.
Compliance with Regulations: The company must consider particular data protection and privacy laws that can apply to the business in specific situations, for example, GDPR or HIPAA.
Best Practices for Regular Audits and Assessments
Security Risk Assessments: Conduct a risk analysis to determine the level of risk that is being posed by the clouds to the entire security infrastructure. Risk analysis required in order to ensure that security measures are deployed to prevent the leakage of data as well as to ensure the protection of the applications.
Policy and Procedure Reviews: Continuously assess and modify security policies and processes over time according to relevant audits or newly identified threats. You should also ensure that the policies in your organization align with the principles of good practice as well as the legal requirements that it has to meet.
Conclusion
Security in cloud computing environments has to be properly implemented to prevent various unauthorized alterations or attacks. Some of the recommended standards for the optimal cloud security include data encryption, stringent identity and access management among others, network security, and efficient handling of security incidents that may occur within a cloud system. Security should remain a moving target while current techniques and methods should be examined and enhanced in order to counter them in the evolving environment of the cloud.
Other factors that need to be considered for higher level security on the cloud:
Advanced Threat Protection
With an increasing sophistication in computer criminals, it is important to get the best in threat protection mechanisms. Organizations should implement advanced security solutions such as:
Machine Learning and AI: Use a machine learning and artificial intelligence powered system to identify threats and manage them in real-time. Security tools that incorporate the use of AI can analyze certain data and recognize certain trends that a human might not be able to detect.
Behavioral Analytics: Use behavioral analytics incidentally to maintain an eye on the activities of the users with a view of identifying malicious activities. It assists in detecting persons within an organisation who pose a threat or whose accounts have been penetrated by a threat actor.
Zero Trust Security Model: Impose a Zero Trust model of security which levies no trust on the systems whatsoever whether they are on the internal or external network. Wherever the access request is coming from, always approve it but only if you are sure.
Secure Software Development
IT professionals must pay much attention to the security of application developed and deployed in the cloud technologies. Organizations should follow secure software development practices, including:
Secure Coding Standards: Implement good practices for coding that keep hackers at bay and avoid trivial issues like SQL injection and XSS.
Code Reviews and Testing: It is also important to review the code on a periodic basis and penetration test the applications to control for major security issues. Since the testing process is tedious and repetitive, it should be automated using testing tools.
DevSecOps: Use Security as a DevOps practice to make security a concern throughout the SDLC to encourage awareness about security concerns in the software development stages. This new approach, referred to as DevSecOps, has become popular because it involves bringing together development, operations, and security specialists.
Container Security
Containers are popular in clouds due to the detachment capabilities and increasing range of uses. Though these devices present new and fascinating opportunities for users, they also pose new security risks. Best practices for container security include:
Image Scanning: While using images to create containers, ensure that the images do not have any vulnerabilities that can be exploited. Make sure you use base images from reliable sources and always keep those images updated.
Runtime Security: Look for signs of unauthorized activities in container run-time environments, as well as ensure adherence to security procedures. The best way to improve the security of the system is to include runtime protection measures that will enable threats to be detected and acted accordingly.
Least Privilege: Implement SU capability for your containers to run them with the minimum level of access to sensitive data. Do not execute the container in root and organize isolation by using name spaces and groups.
Secure Hybrid and Multi-Cloud Environments
Here we present safe ways to launch, operate, and extend applications and services across Hybrid and Multi-Cloud environments. Securing these environments requires additional considerations:
Consistent Security Policies: Ensure that Security Policies are followed as practiced across the multiple cloud environments. To address the second issue, you should implement centralized management tools to put down policies and check compliance.
Inter-Cloud Security: Maintain a consistent but secure connection between various cloud regions or between an on-premise data center and a cloud provider. Ensure that information being sent to or received from other parties is protected while in transmission by employing secure and encrypted application programming interfaces.
Visibility and Monitoring: Monitor all cloud practices and log activities centrally for all the environments that the firm works with. Employable, use SIEM tools to gather intelligence data from different layers and store them to identify threats.
Conclusion
First of all, it is important to note that security of the cloud computing is an ongoing process that begins from the moment of its implementation and lasts at any stages of usage, along with constant emergence of new threats. Thanks to the proper adherence to the recommendations given in this article, organizations will be able to build a reliable and safe cloud environment that defended data from threats and simultaneously promoted business initiatives. Stay proactive, stay informed.
Follow Me for regular Updates on LinkedIn; Twitter; Facebook & Instagram for all Technology Articles
View My other Blog posts Here
Join Us on GRK Connect @ Telegram; Discord & LinkedIn Groups for Discussions on Technology
My Achievements & Projects

This 27-year-old has done record certifications
Govind Ramachandran

Systems Engineer Of Thiruvananthapuram, Kerala, India Gets Included By World Book Of Records

Most number of online IT course certifications – cumulative
Govind Ramachandran
My Resume & Portfolio
Job Experience
IT Analyst
TCS - (October 2023 - December 2023)L3 Azure and Windows Administrator Specialist
Associate II - CIS
UST - (February 2020 - June 2023)Windows & Azure Infrastructure L2/L3 Support Specialist
Support Engineer
SC Soft (September 2018 - July 2019)L1/L2 Support Monitoring Engineer
Freelancer
Freelancer ( February 2015 - August 2018 & July 2019 - February 2020)G Suite and Office 365 Administrator, Technical Analyst & Digital Marketer
Education Qualifications
BA Communicative English
University of Kerala (2014 - 2017)Main : English and Communicative English
Higher Secondary
SNVHSS, Anad (2011-2013)Plus Two Computer Science
SSLC
Darsana EMHSS (2000 - 2011)Elementary Education
Skills
Microsoft Azure
ITIL Certified
IT Operations
Technical Support
IT Service Management
Microsoft Certified Systems Engineer
Skills
Azure Active Directory
IT Asset Management
Server Administration
Google Workspace Admin
Business Strategy
Photoshop
Job Experience
Creator
GRK ( 2025 June Onwards )Token Creator and Investor
Founder
GRK Foundation ( 2024 Onwards )Onwer and Management Activities
IT Analyst
TCS - (October 2023 - December 2023)L3 Azure and Windows Administrator Specialist
Associate II - CIS
UST - (February 2020 - June 2023)Windows & Azure Infrastructure L2/L3 Support Specialist
Support Engineer
SC Soft (September 2018 - July 2019)L1/L2 Support Monitoring Engineer
Freelancer
Freelancer ( February 2015 - August 2018 & July 2019 - February 2020)G Suite and Office 365 Administrator, Technical Analyst & Digital Marketer
Volunteering Projects
Founder and Creator
Color Orange Core Member
UST ( 2022 - 2023 )
Company Experience
IT Analyst
Tata Consultancy Services - (October 2023 - December 2023)L3 Azure and Windows Administrator Specialist
Associate II - CIS
UST - (February 2020 - June 2023)Windows & Azure Infrastructure L2/L3 Support Specialist
Support Engineer
SC Soft (September 2018 - July 2019)L1/L2 Support Monitoring Engineer
Freelancer
Freelancer ( February 2015 - August 2018 & July 2019 - February 2020)G Suite and Office 365 Administrator, Technical Analyst & Digital Marketer
Testimonials & Recommendations

Richin R Chandran
Chief Executive Officer @ RichinnovationsCloud Infra Specialist
I strongly recommend Mr. Govind for your IT and Infrastructure department. I have been associated with him for some projects for the same and understood his commitment and experience. He is a promising professional and experienced candidate in CIS & IMS. I am wishing him all the success for his future endeavours.

Sneha Kappuva Veettil
Cloud DBA SpecialistTechnical Specialist
Govind is one of the most dedicated, hardworking, and innovative people I've had the pleasure of working with within any capacity. He is also compassionate, kind and never misses the opportunity to help others. His talent and actions are helping to achieve excellence in CIS & IMS. I strongly recommend Govind, who is organized, effective, and committed to getting the job done. He'd make an excellent addition to the team. Good Luck Govind !!!

Unnimaya J S
Developer III - Software Engineer @ USTBest Technical Specialist
Govind is an idealistic person and has in-depth knowledge in whatever he is trying to access to. He has an immense understanding in technologies and people too. Govind is keen to acquire knowledge in all platforms and is a person who keeps on learning many things for his carrier growth and has excellent coordinating skills. Govind is a versatile person and will try his best to achieve his goals and making up a project. Good Luck for your future endeavors!!!
Contact Me



















